Registration and Removal
When a new user joins the project for the first time, they will not have access
to the system — it would be a bit concerning if they did! The diagram below
demonstrates the missing piece for a new user, assuming they have already ran
kanuka secrets create and committed their changes to version control.
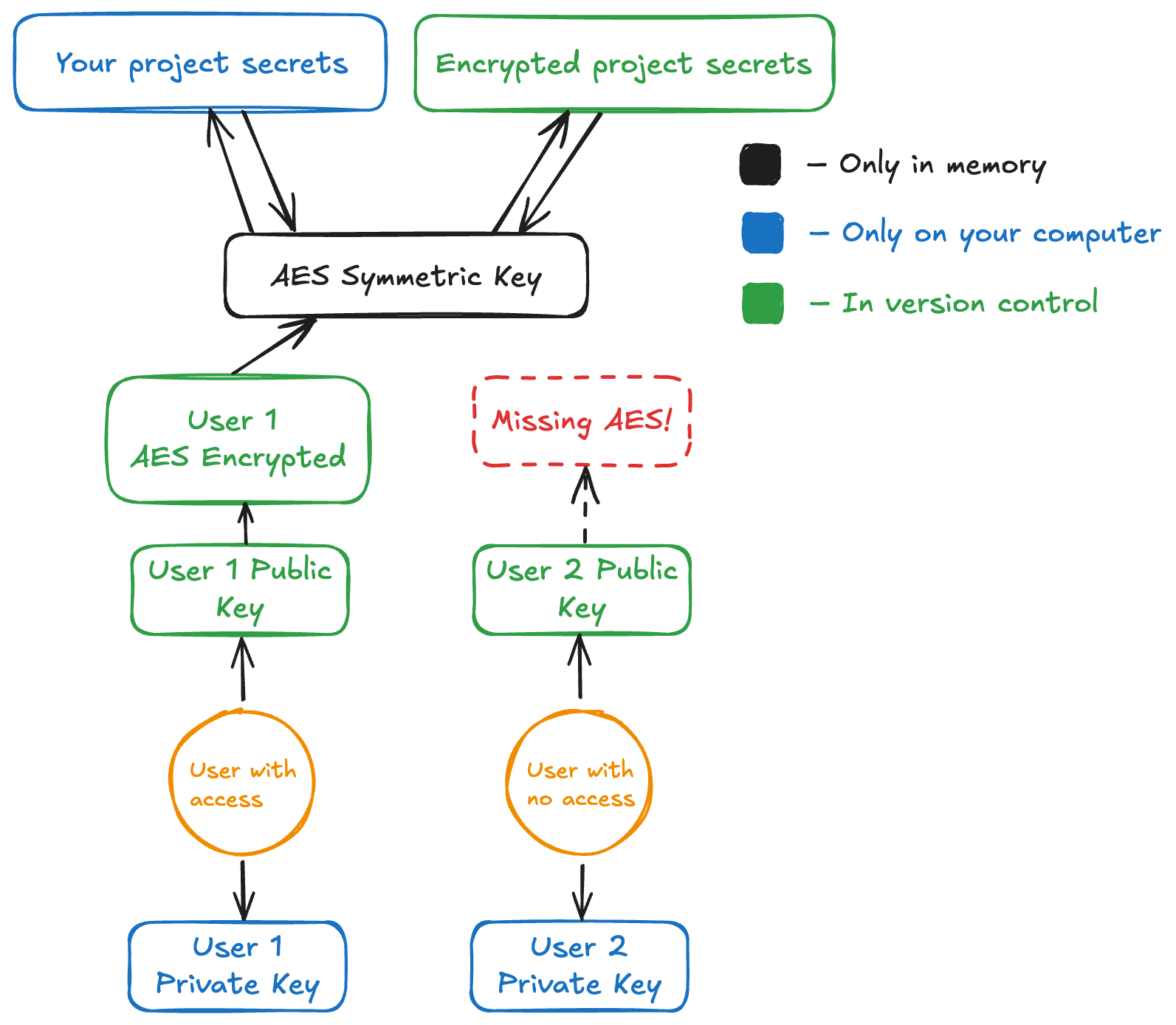
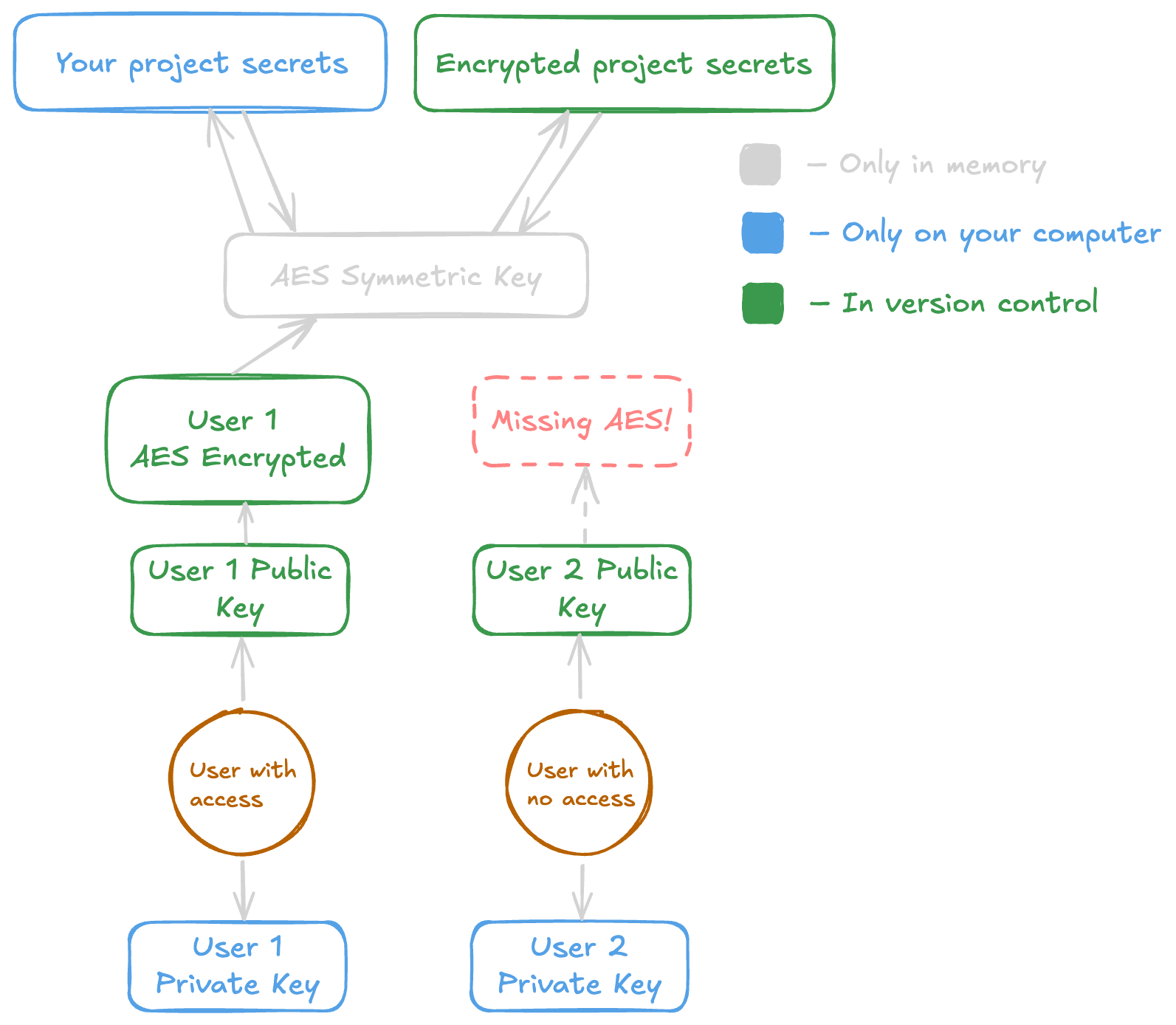
When a user with access runs:
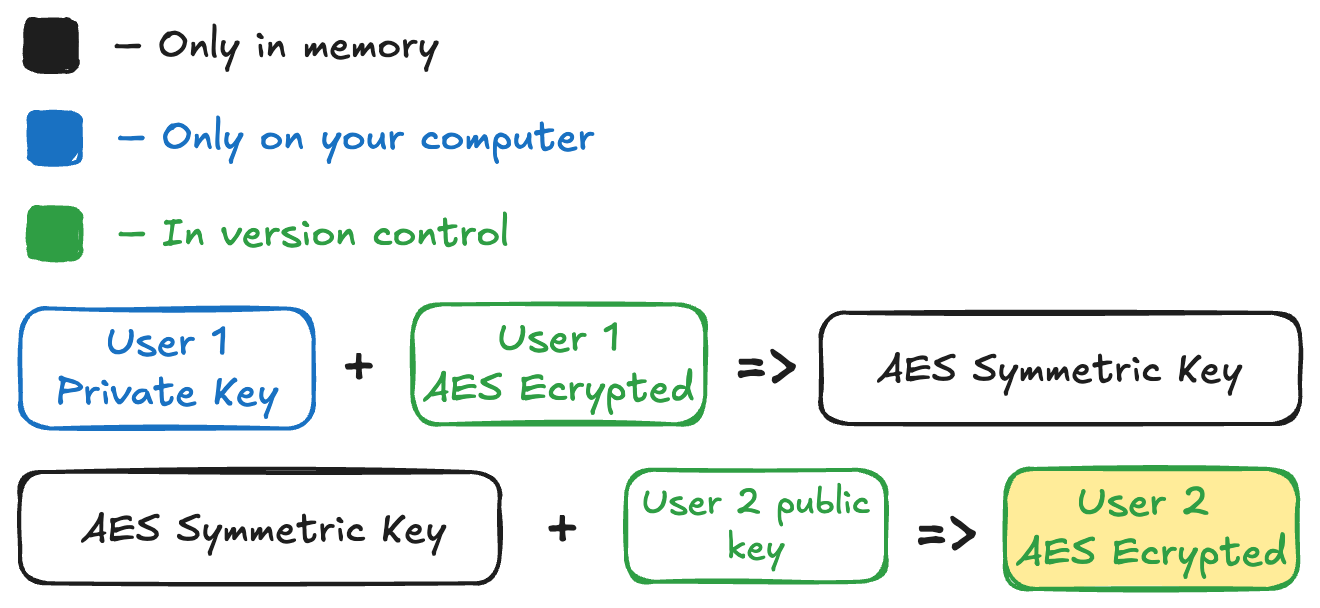
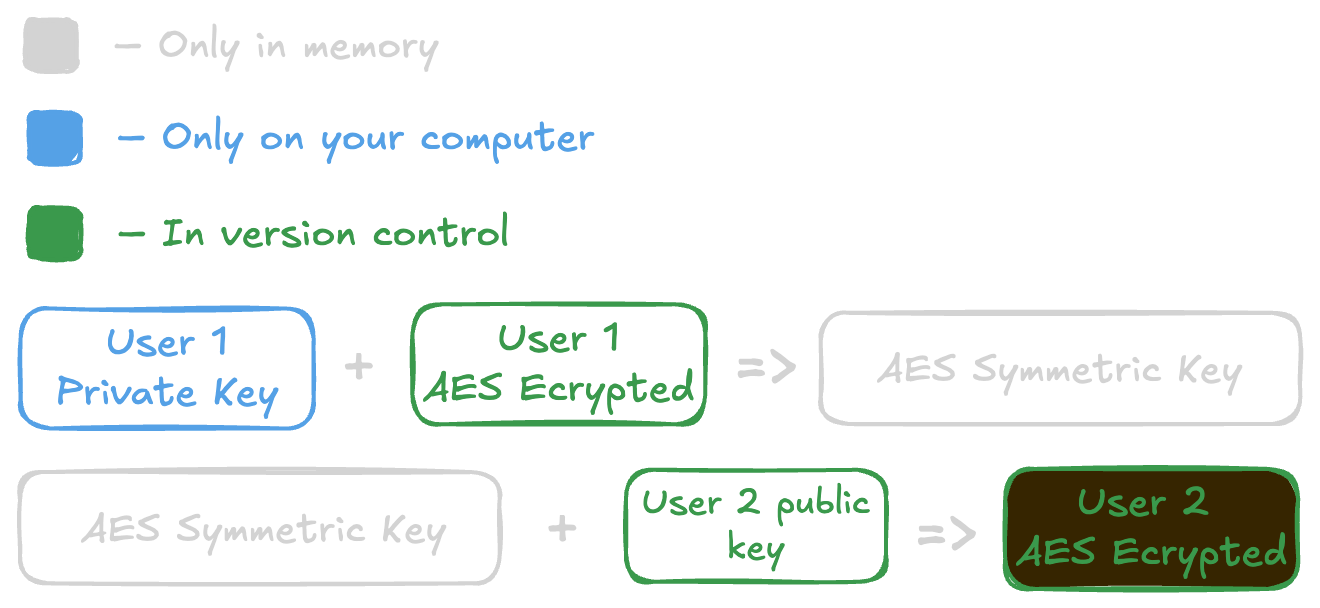
# Using the example's usernamekanuka secrets register --user user_2Kānuka does the following two steps:
- Kānuka will decrypt
user_1’s encrypted AES key. - Kānuka will then use the symmetric key and combine it with
user_2’s public key.
How does Kānuka handle both OpenSSH and PEM format?
Section titled “How does Kānuka handle both OpenSSH and PEM format?”If the RSA encryption standard is like a destination, OpenSSH and PEM are the different ways to get there. At the end of the day, they are both representations of the same thing. Under the hood, Kānuka converts everything to PEM format before using or storing it.
How does Kānuka revoke other users?
Section titled “How does Kānuka revoke other users?”By simply deleting a user’s encrypted AES key and their public key, that user will no longer have access to the secrets, and no other user can accidentally give them access again.
As an extra level of protection, Kānuka will also automatically rotate the AES
key for everyone else so that from that revoke onwards, the revoked user cannot
access the new .env file, even if they restored their old public key.
Continue reading to find out more about configuration within Kānuka.